In my last post, i blogged about UTM’s which got a fairly positive response over mail :) . 
Later on as technology evolved, and hardware routers came into scene, hardware firewalls arrived which were nothing more than routers with packet filtering capabilities. Furthermore, the technology matured from basic packet filtering to a more complex control technology which included stateful packet inspection and finally to full application layer inspection devices (IEEE, 1997). Around the year 2000, VPN’s appeared and gained acceptance as the mainstream technology to connect networks securely, remotely. Firewalls followed closely by integrating VPN’s with Firewall which was the natural choice as enterprise solutions required both firewalls and VPNS.

As the prices for bandwidth fell along with the cost of cryptographic hardware needed to encode and decode the traffic, the need for specialized hardware rose which may be used to accelerate the performance.
Unified Threat Management
In mid 2004, International Data Corporation (IDC) defined UTM platforms as to minimally include firewall, VPN, intrusion prevention and antivirus features. Touted as “Next Generation Firewalls”, we have two approaches to design the UTM’s since their inception.
- Licensing and Integrating Approach (Multi vendor UTM)
- In-house Development Approach (Single vendor UTM)
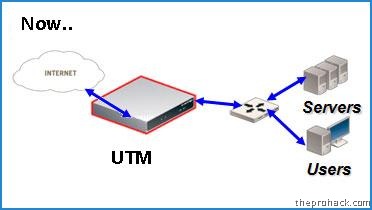
The above figure illustrates the core architecture and development approach of developing UTMs
Licensing and Integrating Approach (Multi vendor UTM)
The first design approach tried to get the best of worlds by integrating specialized technologies from different security vendors. For e.g.:
Cyberoam UTM licenses Antivirus from Kaspersky, AntiSpam by Commtouch , both who specialize in Antivirus and AntiSpam technologies.
These UTM’s provided an integrated interface to manage all the integrated technologies in the easiest possible manner, while some others require specific management interfaces.
| Advantages | Limitations |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
In-house Development Approach (Single vendor UTM)
| Advantages | Limitations |
|
|
|
|
|
|
|
|
| |
|
In my next article I will be discussing more about UTMs. Please add your points so I can make it better.
Stay tuned.

 technologies which I would like to share out with you. I am working along
technologies which I would like to share out with you. I am working along 

 routing products offered by Cisco, 3-Com, Accend, Nortel etc. While all of these companies offer products that are well made, the overhead and overall costs can be expensive.FREESCO is open source, stable, inexpensive, easy to use, extremely versatile and flexible ... and best of all, its is FREE.
routing products offered by Cisco, 3-Com, Accend, Nortel etc. While all of these companies offer products that are well made, the overhead and overall costs can be expensive.FREESCO is open source, stable, inexpensive, easy to use, extremely versatile and flexible ... and best of all, its is FREE. Actually , this time I am covering the basics using GNS3 which is a powerful open source network simulator to simulate a simple topology of 2 routers with their basic configuration & commands. I assume you have worked with GNS3 or atleast know how to load IOS & make a simple topology..
Actually , this time I am covering the basics using GNS3 which is a powerful open source network simulator to simulate a simple topology of 2 routers with their basic configuration & commands. I assume you have worked with GNS3 or atleast know how to load IOS & make a simple topology.. 





 If you are reading this article as a starter / for the first time & have missed the last one, I highly recommend you to
If you are reading this article as a starter / for the first time & have missed the last one, I highly recommend you to  copies it & uses the information to improve its own results. Of course
copies it & uses the information to improve its own results. Of course