There has been a lot of commotion in the Indian Hacking scene lately, and I expressed some pretty strong views regarding that.
 When it comes to hacking, every other guy tends to tape the "hacker" word with his name/codename without even realizing its significance. Then there is Facebook ...Have a look at it -
When it comes to hacking, every other guy tends to tape the "hacker" word with his name/codename without even realizing its significance. Then there is Facebook ...Have a look at it -
Seriously guys..what were they thinking ?! I am still counting the number of “Indian Cyber Army” India has and the number of groups tend to increase recycling all the content, same VIP forums, same deface techniques, zero original research.
Then there is Ankit Fadiya...dont let me even get started...
In the end tired of all the bullshit around, I decided to cover an article on the REAL INDIAN HACKERS (or Hackers of Indian Origin), folks who are actually dedicated to security and are hackers in real sense. Lets start, shall we ?
Pranav Mistry

The famed 6th sense developer,Pranav Mistry is a research assistant and a PhD candidate at MIT Media Lab. SixthSense has recently attracted global attention. Among some of his previous work, Pranav has invented Mouseless - an invisible computer mouse; intelligent sticky notes that can be searched, located and can send reminders and messages; a pen that can draw in 3D; and a public map that can act as Google of physical world. Pranav has commercialized his invention, the sixth sense and SixthSense is now being actively used at NASA. It is rumored that Facebook tried to acquire the technology from Pranav for a reportedly $2 billion and 5% ownership of Facebook, but Pranav decided to open source it instead.

Thats what any real hacker do. Hats Off to him.
Here you can read more about him at Amarjit’s Blog
Koushik Dutta or “Koush”

“Set Your Phone Free..”Rings a bell ? Koushik Dutta or “Koush” is responsible for Clockworkmod recovery and Rom Manager for Android rooting and the core member of famed UnrEVOked team. He has been a .net developer from heart and had his internship initially at Microsoft and is a former MVP. He decided to leave Microsoft and hack Android cellphones like there was no tomorrow. Sony approached him after geohot humped them like anything but he politely declined .

Bravo for his efforts, we are able to root painlessly using UnREVOked.
Now only if UnrEVOked can release UnrEVOked 3.33 soon :)
Vivek Ramchandran

Vivek Ramachandran has been working in the computer and network security domain, in some form or the other, for the past 7 years and has worked with Industry giants like Reliance, Cisco, Microsoft. He was among the Top 10 Indian finalists in the Microsoft shootout competition among the list of 65000 participants. Then he decided to join Airtight Networks and there discovered Caffe Latte attack attack along with his colleague MD Sohail Ahmad from Airtight Networks ,the wifi hacking technique that doesn't required you to be in active vicinity of the wifi zone.
That said, he is one of the researcher to lookout.
Almost everybody at NULL Security Community & Garage4hackers
I said it before and I will say it again, the Only active Indian hacking community is NULL community, and the best Indian Hacking Forum where real hackers meet is garage4hackers.com hands on.

Shoutz to garage crew :)
Folks at Indian Honeynet Chapter
Now we are talking..Indian Honeynet chapter is the collaborative effort of the best geeks and hackers .The focus of honeypot is on Worms and Botnets and developing an Open Source tool to study and counter brute force attacks/ phishing through wifi. Its also being setup as potential web-app honeypot,and aims on improving detection and forensic techniques. Heading the ship are L Shriram, K K Mookhey, Amit Chugh, Asim Jakhar and a lot of professionals who are dedicated in the field of computer security.
Hari Prasad

The famed security researcher Hari Prasad is the winner of EFF Pioneer award, as he along with Alex Halderman, and Rop Gonggrijp were able to study an electronic voting machine (EVM) and found significant vulnerabilities that would not be difficult to execute. For his troubles, Prasad was arrested and jailed in August, held without bail in Mumbai for a week. Though he is now out on bail and in the United States, he still faces criminal prosecution for alleged theft of the EVM and other charges.
The genius of the Indian system is that instead of making machines tamper proof and more efficient, they arrested him.
According to the Indian news agency PTI, the magistrate who released Prasad on bail noted that "no offence was disclosed with Hari Prasad's arrest and even if it was assumed that [the electronic voting machine] was stolen it appears that there was no dishonest intention on his part...he was trying to show how [electronic voting] machines can be tampered with."
Jayant Krishnamurthy

Jayant Krishnamurthy is a Ph.D. candidate in Computer Science, CMU and his interests include are machine learning, machine reading, common sense reasoning, information extraction, knowledge representation, and their applications in AI and NLP (shamelessly taken from his website). He is one of the researchers who are behind designing MD6 algorithm (yeah you heard it right, the evolution of MD5). He is a top level computer theorist and researcher and is a real life hacker. He teaches computer and network security and you must ahve a look at the problems and solutions at the given link.
For the lighter side,you can have a look at the funny flash movie based on his real life experiences at high school.
I guess, you now have an actual idea of the Indian hackers now :) These guys are real and are deemed worthy of having the hacker emblem with them.


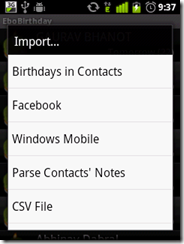



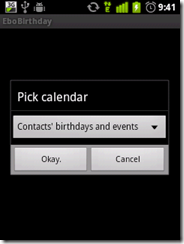

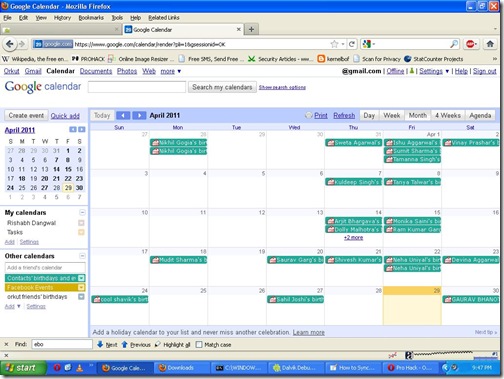
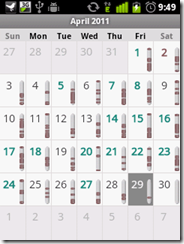


 more "creative" i was stopped by the binded nature of phone, hence i decided to root it (jailbreak it apple fellas) and get complete control over my device. Here, I am covering step by step guide to root HTC wildfire 2.2.1 and install Android 2.3 on HTC Wildfire.
more "creative" i was stopped by the binded nature of phone, hence i decided to root it (jailbreak it apple fellas) and get complete control over my device. Here, I am covering step by step guide to root HTC wildfire 2.2.1 and install Android 2.3 on HTC Wildfire.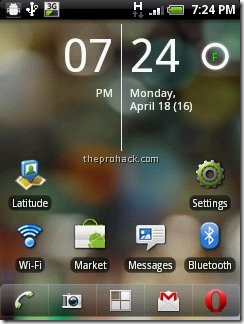





 inaugural event in EC-Council’s new technical IT security conference series - will be taking place from May 14-19, at the InterContinental Dallas, in Dallas, TX.
inaugural event in EC-Council’s new technical IT security conference series - will be taking place from May 14-19, at the InterContinental Dallas, in Dallas, TX. 
 techniques. It is held annually in Montreal, Canada.
techniques. It is held annually in Montreal, Canada. 
 Anyways, to get to the mother load of the downloading, you need access to the alt.binaries content and for that, you need to buy access. Really Sorry! But Usenet isn't a p2p and you have to pay for
Anyways, to get to the mother load of the downloading, you need access to the alt.binaries content and for that, you need to buy access. Really Sorry! But Usenet isn't a p2p and you have to pay for 




 hackable SSL is. SSL has been compromised recently in the RSA hack, and the study exposes the very causes of the broken implementations of SSL and its inherent weaknesses. The article is a must read, here is an excerpt from the original article -
hackable SSL is. SSL has been compromised recently in the RSA hack, and the study exposes the very causes of the broken implementations of SSL and its inherent weaknesses. The article is a must read, here is an excerpt from the original article -  can also be used successfully against Window Media Player. The exploit can be used to perform a
can also be used successfully against Window Media Player. The exploit can be used to perform a  applications. Once it detects one or more SQL injections on the target host, the user can choose among a variety of options to perform an extensive back-end database management system fingerprint, retrieve DBMS session user and database, enumerate users, password hashes, privileges, databases, dump entire or user’s specified DBMS tables/columns, run his own SQL statement, read or write either text or binary files on the file system, execute arbitrary commands on the operating system, establish an out-of-band stateful connection between the attacker box and the database server via Metasploit payload stager, database stored procedure buffer overflow exploitation or SMB relay attack and more.Enthusiastics can experiment with its opotions and pwn many of the servers around,or can test their skills to secure their servers..but remember,SQL map is a tool,its might help you to find and
applications. Once it detects one or more SQL injections on the target host, the user can choose among a variety of options to perform an extensive back-end database management system fingerprint, retrieve DBMS session user and database, enumerate users, password hashes, privileges, databases, dump entire or user’s specified DBMS tables/columns, run his own SQL statement, read or write either text or binary files on the file system, execute arbitrary commands on the operating system, establish an out-of-band stateful connection between the attacker box and the database server via Metasploit payload stager, database stored procedure buffer overflow exploitation or SMB relay attack and more.Enthusiastics can experiment with its opotions and pwn many of the servers around,or can test their skills to secure their servers..but remember,SQL map is a tool,its might help you to find and