 It all started with me hunting for a point and shoot camera for my mother. To be frank , any camera with no hassles & fair performance would have qualified and I was personally looking for Nikon L26; but since it was deemed out-dated by Nikon itself, I hopped in for Nikon L27 violet colour camera. Now, to be frank I never wanted to go out of Flipkart/Infibeam since they have stood the test of time with me, but somehow I ordered it from another popular online portal Snapdeal.com & there the things start to get interesting.
It all started with me hunting for a point and shoot camera for my mother. To be frank , any camera with no hassles & fair performance would have qualified and I was personally looking for Nikon L26; but since it was deemed out-dated by Nikon itself, I hopped in for Nikon L27 violet colour camera. Now, to be frank I never wanted to go out of Flipkart/Infibeam since they have stood the test of time with me, but somehow I ordered it from another popular online portal Snapdeal.com & there the things start to get interesting. For starters, I never received any email of purchase confirmation, I thought it might have landed in junk/spam folder but hell no. I double checked my email filters, searched every label but nopes..zilch..nada..I simply didn't get any email receipt of purchase from Snapdeal. It was the first omen of a Bad Deal (aka Snapdeal) . Thankfully I didn't closed my browser windows, I was lucky to take the snapshot of transaction , noted down the transaction id from my bank statement , drank a glass of water & wiped away the sweat that scorching Delhi summer delightfully gave me.
5 minutes later I received an SMS from Snapdeal regarding my order number, I matched it with my snapshot, went online again and found after providing my details, the estimated shipping date was 20th May 2013.
I tried to login into Snapdeal and found that since I created an account long time ago (when Snapdeal was not into store business and was into deals business) , I didn't actually remembered its password. I tried to reset it, but received *NO EMAIL* from Snapdeal. Now that was alarming, I was not able to reset my password, not able to get an email receipt and I was not very sure about the delivering capability of Snapdeal (quick search on mouthshut.com was quite revealing).
Immediately I called customer care (+91-92126-92126) , after hearing to whistles and caller tune for 5 minutes (yes, *5 minutes*) , my call was picked. I explained to CCE -
- I am not getting email from Snapdeal.
- I did not received an receipt.
- I am unable to reset my password.
- What is the status of my order as of now and by what time will it get delivered.
- He can not reset password nor help me in any regards in account or email issue.
- My order was under processing and he can not provide an estimated delivery date.
Also, I logged into Snapdeal via FB authentication and was still not able to reset the password.
That was on 15th May 2013.
Now ,to be frank I have never ordered anything from Snapdeal before, one of my friends (Gurpreet Singh) had once ordered some stuff from it , but he warned me about Snapdeal's performance issues after I placed the order.
While I was gleefully cursing him "Saaley pehle kyu nahi bataya !!" , he reassured me that they are slow but they atleast deliver the goods.
"Also, shipping date is 20th,you might be getting goods before that in your hands", he finished gulping his last glass of lassi.
Nervously I reassured myself and crossed my fingers. Who knows, It wasn't for me, it was for my Mom and I wanted to get it delivered on a timely manner.
17th May came and status was still "processing" on the website. Furthermore I tried calling to customer care thrice with no one responding on the number. They also hanged up on me on one occasion without CCE interaction.
Now I was getting a bit angry. 18th May, it was Saturday noon and order was still under processing. I tweeted to Snapdeal
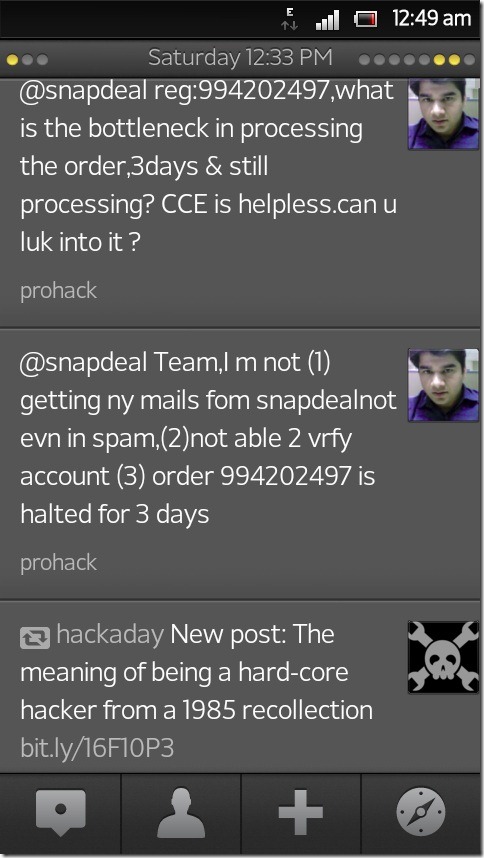
No response from Snapdeal as of now. Also, I sent the email to Snapdeal helpdesk (help@snapdeal.com)
Team,You guessed it right, no response from Snapdeal.
I bought Nikon Coolpix L27 16MP Point & Shoot Digital Camera (Purple) Order Number 994202497 Item code 1333471211, its been 3 days but I have NOT received the email reciept of order. Further more I am not able to verify my snapdeal account as I am not getting any emails from Snapdeal regarding verification and order.
I have looked into SPAM/JUNK folder to no avail. I mentioned the same to customer care on 9212692126 but they were helpless.
Furthermore, Why is it so much delay in processing the order ? 3 days and its still processing. Whats the bottleneck in it ? I never had such slow response from any of online retailers I have used ?
Please get back to me on the double.
On 20th May I shot another one.
Dear Team,
Still awaiting your response. Its quite incredulous that I am following up for an email response which should have been your duty . Its 20th may and the product page still shows shipping date of 20th May with no update. I had a word with CCE Maninder Sandhu (yeah I got lucky, finally your customer care picked the call) for an update on the order but then he himself was helpless regarding the same.
Its pathetic how you are keeping the money interest free without giving any proactive updates on the status of order and keeping customer completely blind on it.
Nevertheless, I will be waiting till 21 May on an update for a fair chance. After that , I will be cancelling the order and will be filing for a refund.
Regards
Seriously, I could have posted call records but then I think it would have been a bit overkill. But then, if they could record our calls for "quality & training purposes" then why cant we use them for some real "quality" purposes ?
I had no idea what was going on, at least an email response would have sufficed. We live in a country where consumer is hailed as king, I have no complains with late deliveries, I am actually angry with no/diminutive response from Snapdeal team. I have paid for an item first rate , online , in single transaction with no dues pending , no instalments and they are keeping my money interest free , processing it according to their whims and are providing no reasons for delay. Furthermore, response time is pathetic, I got the reply from Snapdeal on Facebook page / Twitter , 2 days later, & that too that they are looking into it and order will be shipped today.

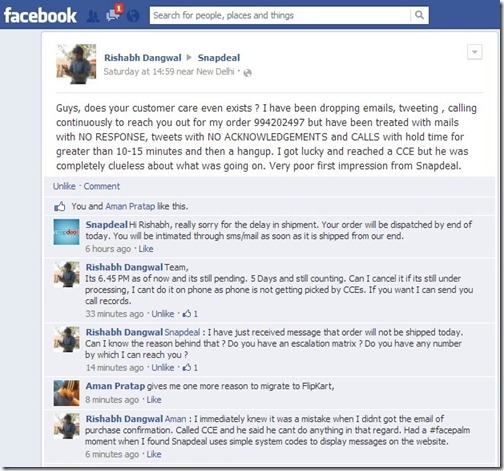
Also, a quick look on their FB page reveals that I am not the only one frustrated from Snapdeal, see the below image or click the mentioned link.

Later, I got an SMS from Snapdeal that order has been delayed.

But the online portal is still showing that order is under processing and I really dont know what information to trust.

I was also not able to cancel my order as I CANT REACH TO CUSTOMER CARE AND I AM NOT SURE IF MY EMAILS ARE EVEN READ. As per Snapdeal's guidelines, they can choose to accept or deny my request of cancelling the order based on their convenience and understanding of situation.

If you cant read it, to quote Snapdeal (Trust me, its an amusing read)
10.2 Cancellation by the User: In case of requests for order cancellations, Snapdeal reserves the right to accept or reject requests for order cancellations for any reason whatsoever. As part of usual business practice, if Snapdeal receives a cancellation notice and the order has not been processed/ approved by Snapdeal, Snapdeal shall cancel the order and refund the entire amount to You within a reasonable period of time. Snapdeal will not be able to cancel orders that have already been processed. Snapdeal has the full right to decide whether an order has been processed or not. You agree not to dispute the decision made by Snapdeal and accept Snapdeal's decision regarding the cancellation.Very cute .
Bet I would have called Snapdeal for cancellation and they would have cancelled my request because they “had processed my order” .. and because its written in clause 10.2 .
As of now, summing up my entire experience on Snapdeal echoes the following problems again and again -
- Lack of proper communication to customer.
- Unresponsive support &
- Broken implementation of information systems.
As of now, I haven't got any response on my tweet to Snapdeal

Another call to CCE Maninder Sandhu (I just got lucky) was fruitless although he was a nice chap and was trying to help.
Lessons learnt :
- I wont be shopping from Snapdeal again, thats for sure, unless they make some really radical changes in their system.
- Wont be ordering from my hard earned money from portals that are pathetic.
Meanwhile, I am still waiting for my camera to be delivered .. : (
(6 Days at the time of writing ) and counting..
Update 21 May 2013 6.04 PM IST :
To top it off as of now -
- Still estimated shipping time on webpage is showing 20th May, but it has been updated that tracking number will be available in 12 hours, so I actually dont know what is the correct update.
- Snapdeal_help on twitter promised a a shipping by today but to no avail . They actually update my Mother and not me regarding that, but alas, its still showing pending.
- According to CCE Akash, package is ready for courier and will be shipped by tomorrow first half. One more date..Lets see how it goes.
- Snapdeal FB page removed the negative comments, however you can see them in the picture which is given above.
Update 21 May 2013 7.00 PM IST :
Got a call from Snapdeal Okhla Office from Monika , provided courier tracking number and apologized for delay, I thanked her. Also, as per her, the tracking number will be active within 12 - 48 hours, I promptly checked the 11 digit tracking number which was not active on Courier service (Bluedart) page. She might be right. Will check it tomorrow morning.
Update 22 May 2013 6 PM IST :
AS of now, Snapdeal has *FINALLY* shipped my order (YAY!!) . But again, it has been delayed by Courier Service. As of now, I was in talks with Assistant Mgr at Courier service who was quite helpful and said the product will be delivered by tomorrow. All I hope it is a functional one as this long delay has shaken my already non existent faith in Snapdeal.
Update 23 May 2013 6 PM IST :
Finally, after numerous delays, Order was delivered. The bottomline ? Well, the issue was already escalated at Snapdeal end , the pity was that when I checked at support.snapdeal.com , my ticket was not updated in 3-4 days, and one was closed with remark that customer (thats me) was not reachable. Excellent, it was only when I started escalating the matter on online and social platforms, they came into action and hasted the matter. Still its 8 days, which is well beyond the norms of a normal e-comm site.
I am glad it all ended well. Mom got the camera and I got to see the inner workings of an e-comm site.
Update 22 May 2013 6 PM IST :
AS of now, Snapdeal has *FINALLY* shipped my order (YAY!!) . But again, it has been delayed by Courier Service. As of now, I was in talks with Assistant Mgr at Courier service who was quite helpful and said the product will be delivered by tomorrow. All I hope it is a functional one as this long delay has shaken my already non existent faith in Snapdeal.
Update 23 May 2013 6 PM IST :
Finally, after numerous delays, Order was delivered. The bottomline ? Well, the issue was already escalated at Snapdeal end , the pity was that when I checked at support.snapdeal.com , my ticket was not updated in 3-4 days, and one was closed with remark that customer (thats me) was not reachable. Excellent, it was only when I started escalating the matter on online and social platforms, they came into action and hasted the matter. Still its 8 days, which is well beyond the norms of a normal e-comm site.
I am glad it all ended well. Mom got the camera and I got to see the inner workings of an e-comm site.













