Hi folks, as you know I am currently at Delhi, at Tulip Telecom, I got my hands on exotic network  technologies which I would like to share out with you. I am working along Amarjit Singh & the rules of the game are simple, he will create a security scenario while I will try to break it. Considering I am a bit novice in network technologies, it has been a highly learning experience with some really great hands on tech demos & real life scenarios. I will be explaining about Unified Threat Management (UTM) today which you can think of an all in one solution to an organizations security needs. Unified Threat Management devices are relatively new in the security appliance scenario & are in the phase of continuous evolution. UTM has attracted industry leaders like Juniper, Fortinet, Cisco, IBM, Intel, Cyberoam & there are a lot of UTM products to choose from. I am however working on the Cyberoam one & will be continuing my tests on it.
technologies which I would like to share out with you. I am working along Amarjit Singh & the rules of the game are simple, he will create a security scenario while I will try to break it. Considering I am a bit novice in network technologies, it has been a highly learning experience with some really great hands on tech demos & real life scenarios. I will be explaining about Unified Threat Management (UTM) today which you can think of an all in one solution to an organizations security needs. Unified Threat Management devices are relatively new in the security appliance scenario & are in the phase of continuous evolution. UTM has attracted industry leaders like Juniper, Fortinet, Cisco, IBM, Intel, Cyberoam & there are a lot of UTM products to choose from. I am however working on the Cyberoam one & will be continuing my tests on it.

A brief history
Earlier, the enterprise security scenario was divided into traditional firewalls & targeted applications like Antivirus, Anti spam & Intrusion Detection Systems.

However in 2004 , a new trend emerged which combined multiple security features into one single hardware platforms thereby eliminating the need of machine to machine protection.
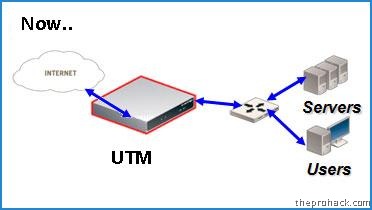
Since its inception, UTM’s are one of the fastest growing segment in the security appliance sector.
Why UTM ?
 technologies which I would like to share out with you. I am working along Amarjit Singh & the rules of the game are simple, he will create a security scenario while I will try to break it. Considering I am a bit novice in network technologies, it has been a highly learning experience with some really great hands on tech demos & real life scenarios. I will be explaining about Unified Threat Management (UTM) today which you can think of an all in one solution to an organizations security needs. Unified Threat Management devices are relatively new in the security appliance scenario & are in the phase of continuous evolution. UTM has attracted industry leaders like Juniper, Fortinet, Cisco, IBM, Intel, Cyberoam & there are a lot of UTM products to choose from. I am however working on the Cyberoam one & will be continuing my tests on it.
technologies which I would like to share out with you. I am working along Amarjit Singh & the rules of the game are simple, he will create a security scenario while I will try to break it. Considering I am a bit novice in network technologies, it has been a highly learning experience with some really great hands on tech demos & real life scenarios. I will be explaining about Unified Threat Management (UTM) today which you can think of an all in one solution to an organizations security needs. Unified Threat Management devices are relatively new in the security appliance scenario & are in the phase of continuous evolution. UTM has attracted industry leaders like Juniper, Fortinet, Cisco, IBM, Intel, Cyberoam & there are a lot of UTM products to choose from. I am however working on the Cyberoam one & will be continuing my tests on it.
A brief history
Earlier, the enterprise security scenario was divided into traditional firewalls & targeted applications like Antivirus, Anti spam & Intrusion Detection Systems.

However in 2004 , a new trend emerged which combined multiple security features into one single hardware platforms thereby eliminating the need of machine to machine protection.

Since its inception, UTM’s are one of the fastest growing segment in the security appliance sector.
Why UTM ?
- UTM’s provide one stop solution for security needs of an organization.
- The integrated approach allows the administrator to worry about only one device, not the whole flurry of firewalls, antiviruses & IDS/IPS.
- Increase in blended attacks against organizations has led to older specialized protection devices/services obsolete.
- Cost effective , tell me one thing, which will be more costlier ? One decent firewall, site licenses of Antivirus, Anti spam, Anti phishing, IDS, IPS etc or a single UTM device with combined subscription costs ? The answer is the second one :)
- One stop reporting solution.
nah..cyberoam :)
ReplyDeletethanks :) Its Acer EEpc
ReplyDelete