Trojan.Jnanabot, or alternately as OSX/Koobface made waves in security scene when it was discovered that it can 
“Even though it's encrypted and even though it was written in Java to make it cross-platform, it was still vulnerable to basically a directory transversal exploit,”
exclaimed Dean Turner, director of Symantec's Global Intelligence Network. He added -
“From a technical perspective, it goes to show that even if you have all those things where you're building in a secure platform, if you're not building application security into your malware, other bad guys will probably take advantage of it.”
P2P function is designed to make botnets harder to take down by providing multiple channels of communication. Once a website sends a single GET request to an infected host, it can discover all the info needed to upload any file to any location on host, furthermore,attackers can then install a simple backdoor & can totally own the machine.
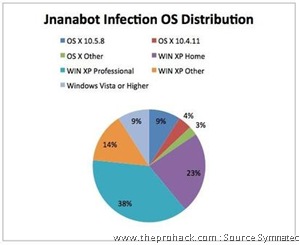
Interestingly, statistics by Symnatec show that the bot’s favorite host platform is Windows - 85 % & Mac comes 2nd by 15 % . They didn't show any infections on Linux machines. Speaking of botnets, you might want to read about Project Blackout too ..
source : El Reg
Like This post ? You can buy me a Beer :)
Posted by XERO. ALL RIGHTS RESERVED.
0 comments:
Need to say something ? Spell it out :)